Phishing (pronounced “fishing”) is the fraudulent attempt to obtain sensitive information or data, such as usernames, passwords and credit card details or other sensitive details, by impersonating oneself as a trustworthy entity in a digital communication. Typically carried out by email spoofing, instant messaging, and text messaging, phishing often directs users to enter personal information at a fake website which matches the look and feel of the legitimate site. Wikipedia
Common Phishing Tactics
Phishing is by far the most common form of cyber-crime reported to the FBI’s Internet Crime Complaint Center (IC3). Common phishing tactics include:
- Messages warning of an impending de-activation or closure of an account, and a link to a website to ‘verify’ your account – which actually steals your credentials. Sometimes they will make the scary claim that your account was compromised and you must prove your identity.
- Offer of a job to the recipient. Usually this is an unsolicited job that offers unrealistically high pay, and with no interview or a few perfunctory questions by email. Eventually, the criminal will either ask for personal information “for payroll purposes” which is actually used for identity theft. Another common tactic will be to ask the new ‘employee’ to purchase some goods – sometimes a list of ‘supplies’ needed for the job or gift cards, with a promise of being reimbursed.
- Urgent messages claiming to be from an executive or other important person asking for a time-sensitive favor, which often involves buying gift-cards and replying with the gift card numbers or photos of the cards.
- Messages claiming to be from a store or common service (such as Netflix) pretending that payment was denied for a recent purchase, and directing you to a (fake) website to have you re-enter your credit card information.
- A forged message from a bank alerting you to an account update you need to perform, or that a fraudulent transaction was suspected and you need to login immediately to resolve it.
- Messages claiming to be from the IRS, the FBI, or other government agencies. Sometimes they get your hopes up and pretend that you have a big tax refund waiting, and sometimes they accuse you of committing some crime or threaten you with penalties.
Protective Measures – Don’t get hooked
Learn to recognize phishing, they often…
- Attempt to build credibility by spoofing a real company or university. Often, the messages are laughably bad, but many are incredibly believable facsimiles of real messages. The most dangerous are personalized specifically for you, referred to as spear phishing, using knowledge about you or your work.
- Create a false urgency requiring a quick response – such as warning that your account will be closed
- Insist on a call to action – urge you to click a link or reply with information
- Do not address you by name or include other information specific only to you
Use common sense when giving out personal information
- Be suspicious by default
- Check the email for fake web links or fake web addresses
- Never give out account or personal information by email
- Remember, UF will never ask you for your password. Only enter your password into the official UF login page: login.ufl.edu.
Verify the information reported in the e-mail
- If in doubt, call customer support or, in the case of UF email, call the UFIT Help Desk at 352-392-HELP to validate the message
- If the message claims to be from someone at UF, look the sender up in the UF Directory and call them using the number listed, or respond to the official email address.
Anatomy of a Phish – “Phish Guts!”
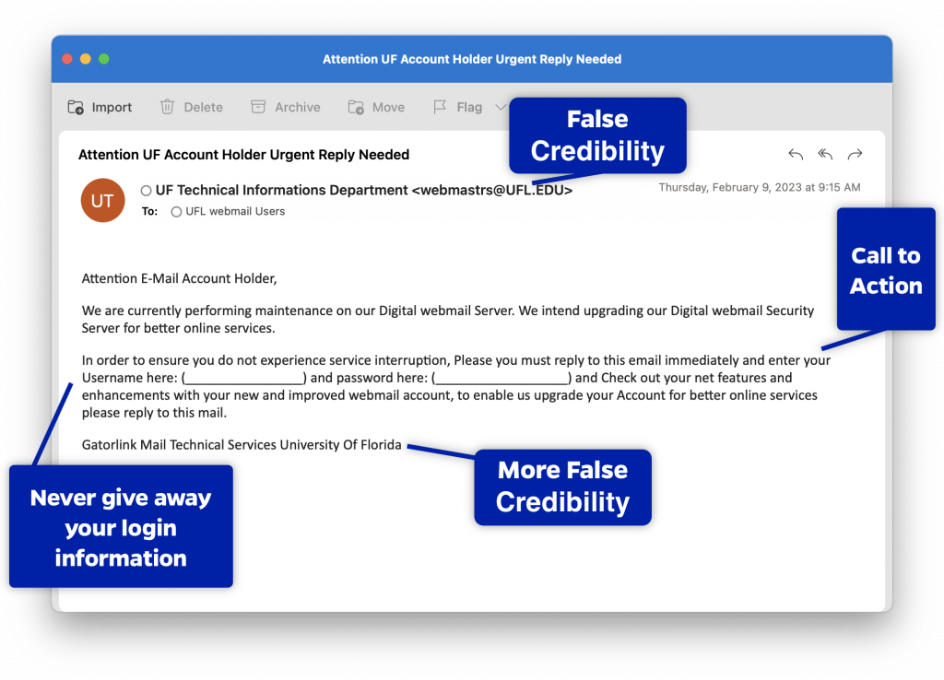
UF Spear Phishing Example 1
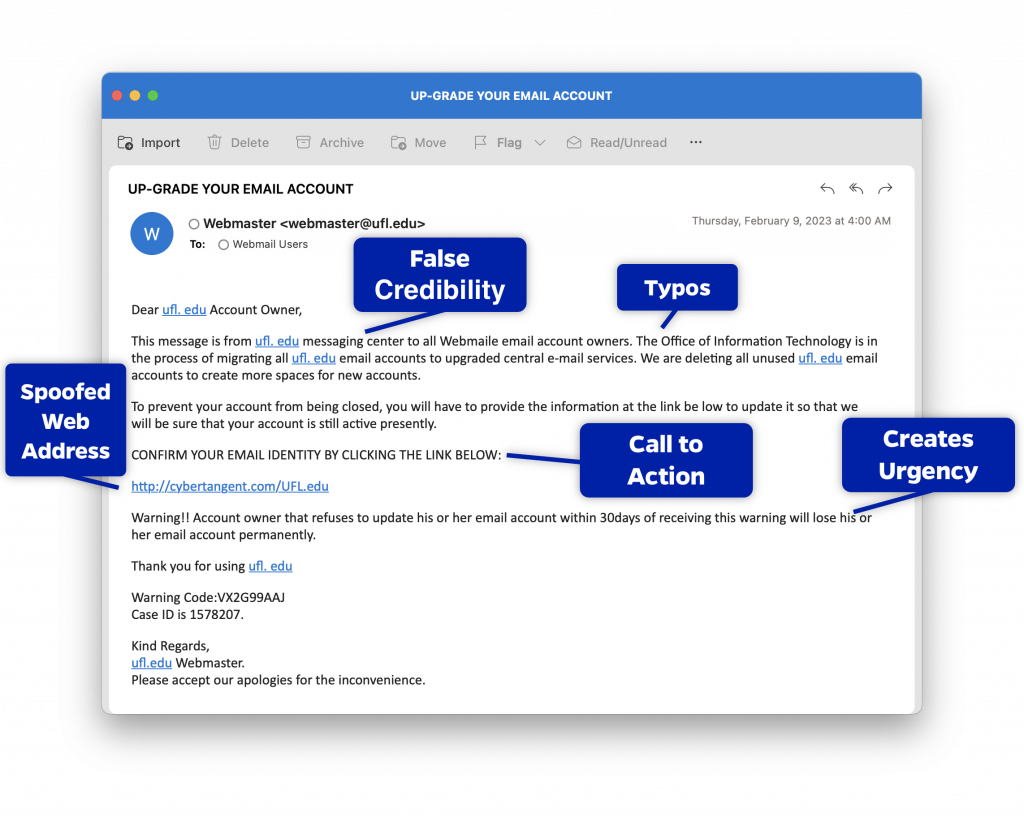
UF Spear Phishing Example 2
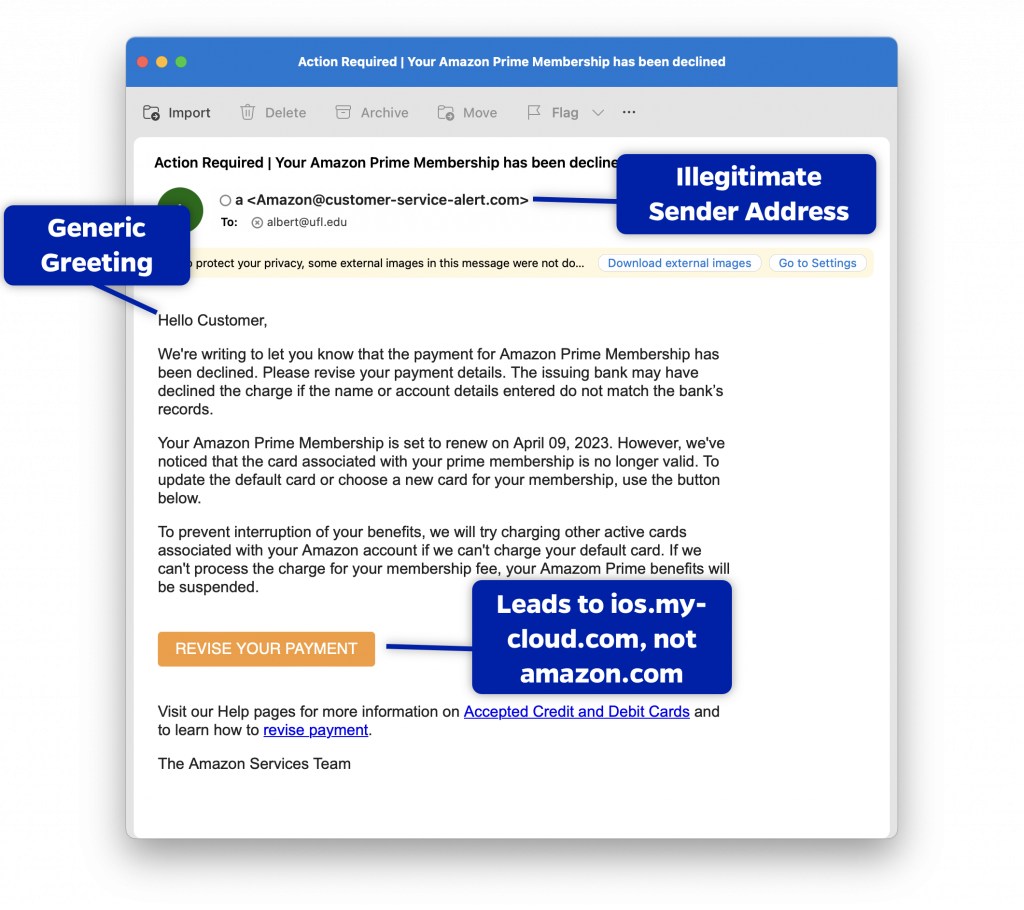
Payment Declined Example
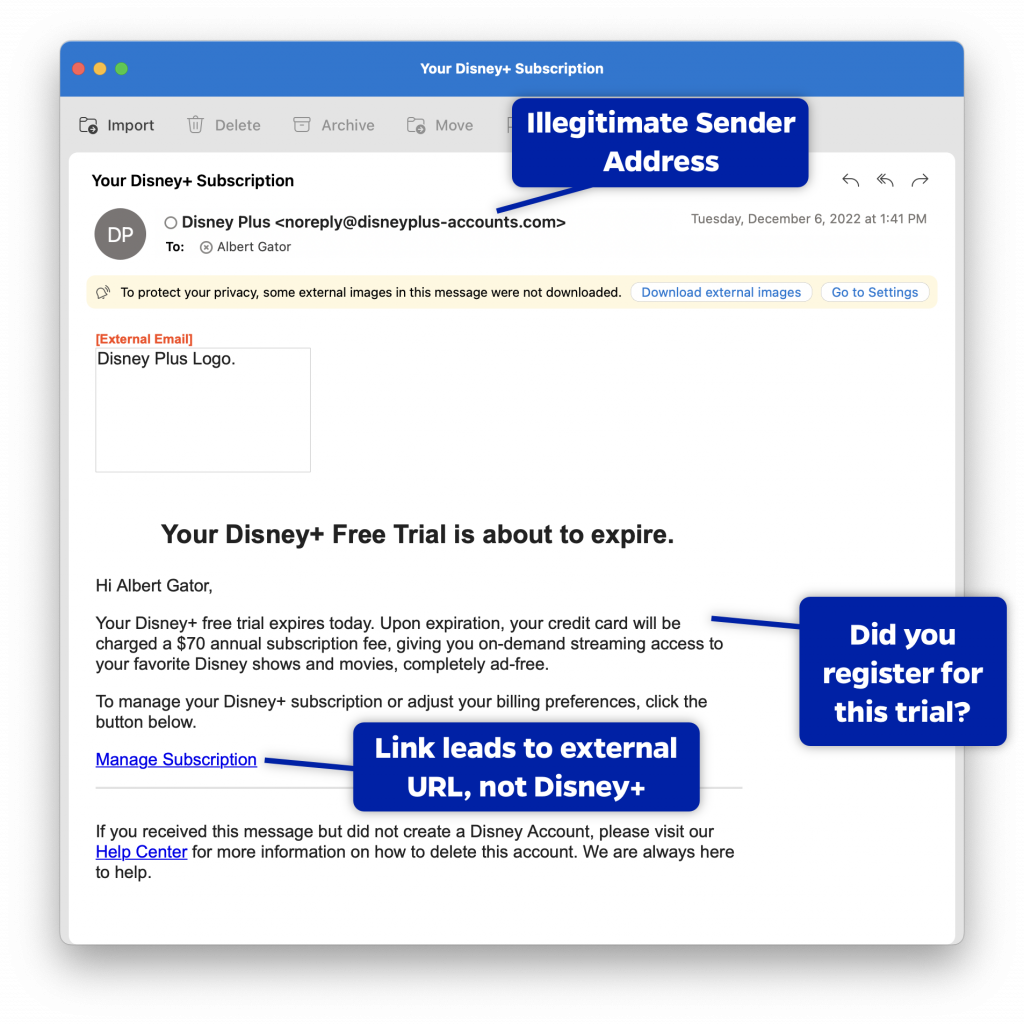
Free Trial Expiring Example
Can You Spot Phishing?
Take this phishing quiz from Google, which presents realistic examples of phishing messages and authentic messages for you to choose from. It will also point out clues to help you identify fraudulent messages.
Report Phishing at UF – show us the headers
If you receive a phishing message that targets you as a UF staff, faculty, or student, you should check the UF IT Security Advisories web page to determine if we are already aware of that particular phishing attack. The best way to report phishing is with the Phish Alert Button in GatorMail (Microsoft 365 Webmail) and installed on many UF-managed Outlook clients.
If you don’t have the Phish Alert Button, you can report phishing attacks by forwarding the original phishing message, with full message headers, to abuse@ufl.edu. It is important that we get the full message with the original routing information (headers) to determine the source of the email and best be able to block it. The easiest way to do so is to choose ‘Forward as attachment’ in your email client.
