UF Cybersecurity Framework (CSF)
 In July 2021, UF will begin a process of assessing maturity against the UF Cybersecurity Framework (UFCSF). This framework is based on the National Institute of Standards and Technology (NIST) Cybersecurity Framework, but tailored to UF’s OneIT model. This project is a collaboration between the UF Information Security Office, the Office of Internal Audit, and the UF’s Compliance and Ethics Program.
In July 2021, UF will begin a process of assessing maturity against the UF Cybersecurity Framework (UFCSF). This framework is based on the National Institute of Standards and Technology (NIST) Cybersecurity Framework, but tailored to UF’s OneIT model. This project is a collaboration between the UF Information Security Office, the Office of Internal Audit, and the UF’s Compliance and Ethics Program.
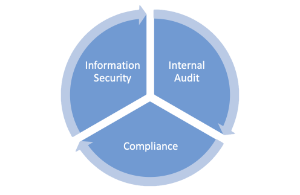
- Information Security manages the assessment and reporting process, and will identify needs for future projects to improve overall cybersecurity maturity, and assist units in growing maturity.
- Internal Audit will perform verification of results, use data that is collected to inform operational audits, and identify institutional risks for future study.
- Compliance will use results to demonstrate compliance with regulatory, contractual, and policy requirements. Results will also be available when responding to external audits.
Enhanced view of cybersecurity risks
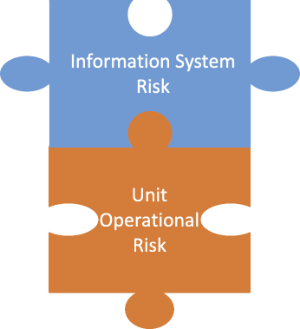
UF already conducts risk assessments at the information system level, which provides a detailed view of the risk of individual systems. The UFCSF will provide a high-level view of the operational maturity of participating units, which will be rolled up into a university-wide maturity rating. This information will be used in several ways:
- Develop a unified view of the university’s security posture
- Identify gaps in enterprise cybersecurity processes and technology
- Institutional results will inform Enterprise Risk Register
- Identify and develop university-wide solutions that will have the greatest impact on risk reduction and increases in cybersecurity maturity
- Provide guidance to units on areas for improving cybersecurity maturity
Organized around the 5 functions of the NIST Cybersecurity Framework
The NIST Cybersecurity Framework is designed around, and intended to complement, the NIST control frameworks (800-53 and 800-171) that UF already uses for individual information systems. Rather than a prescriptive set of controls that must be implemented, units can select from multiple answers and choose one that most closely corresponds to how cybersecurity is actually implemented. These answers are then used to calculate a maturity level, both at the individual sub-category and rolled up for an overall view of the unit. It is expected that different units will be at different levels of maturity. The first year of assessment will be used as a baseline, after which targets will be set for units based upon their characteristics and security requirements. The Information Security Office will then provide recommendations for units to increase maturity where needed.
Assessment Process
The assessment will be conducted through surveys in the Archer platform. College-level IT directors will identify units to participate, and units will nominate the appropriate person to complete the surveys – usually the Information Security Manager (ISM). The entire assessment is separated into four quarterly surveys, of 20-40 questions each.

After each survey is completed, the Office of Internal Audit will perform verification by contacting the survey respondents for additional information on selected questions in order to maintain consistent results between units.
Once verification is complete, units will be provided with reports describing the assessed maturity level. After the initial baseline year, reports will include progress toward the targeted maturity level and recommendations to increase maturity.
Reports will be rolled up to produce overall maturity level metrics for the university and identify systemic gaps that could be addressed with enterprise solutions. These reports will be provided to university leadership.
